
Published 7 December 2022 – 16 min read
By Rebecca Archambault, Felix Gaehtgens, James Hoover, Ant Allan
Decentralization of computing resources, channels, entities and devices makes traditional perimeter-based security strategies and tools insufficient. Security and risk management leaders must put identity at the core of cybersecurity strategy and invest in continuous, context-aware controls.
Overview
Key Findings
- The broad adoption of cloud services, digital supply chains and remote access by employees working from anywhere has eroded the value of legacy security controls at the perimeter of the corporate network, positioning identity as the primary control plane for cybersecurity.
- Static, inflexible and high-level identity and access management (IAM) policies are no longer a sufficient source of trust; they don’t take into account the continuous and context-aware controls needed to identify and respond to changes in risk and trust throughout the user journey.
- Traditional IAM controls are defined to address a particular risk or audit finding, based on static rules or schedules, providing “checkbox compliance.” This legacy approach fails to address security risk pervasively or in real-time.
Security and risk management leaders focused on IAM should:
- Think “consistent”: Achieve Identity-first security by adopting access policies to enforce access by moving past static protection architectures and focusing on dynamic controls.
- Think “context”: Ensure flexible, scalable and risk-based access by identifying what contextual data is available, from which sources, and defining dynamic context-aware policies.
- Think “continuous”: Improve the efficacy of access decisions by using continuous risk and trust assessment and applying controls throughout entire sessions, rather than using simple “gating” decisions to let users in.
Strategic Planning Assumption
The legacy approach to IAM fails to address security risk pervasively or in real-time — nor does it align with zero trust strategies. Quick Answer: How to Explain Zero Trust to Technology Executives sets out three key principles of zero trust:
- Establish the right level of trust dynamically.
- Assume that the organization has been compromised.
- Use identity and context.
Identity is a core foundational element of a zero trust strategy and is typically the starting point for many organizations looking to implement zero trust controls. To enable zero trust and optimize the organization’s cybersecurity posture, an IAM leader must realign IAM investments to enable identity-first security.
Identity-first security is an approach that makes identity-based controls the foundational element of an organization’s cybersecurity architecture. It marks a fundamental shift from reliance on static perimeter-based controls that have become obsolete due to decentralization of computing resources, channels, entities (human and machines) and devices.
Figure 1: A Three Cs Approach to Identity-First Security
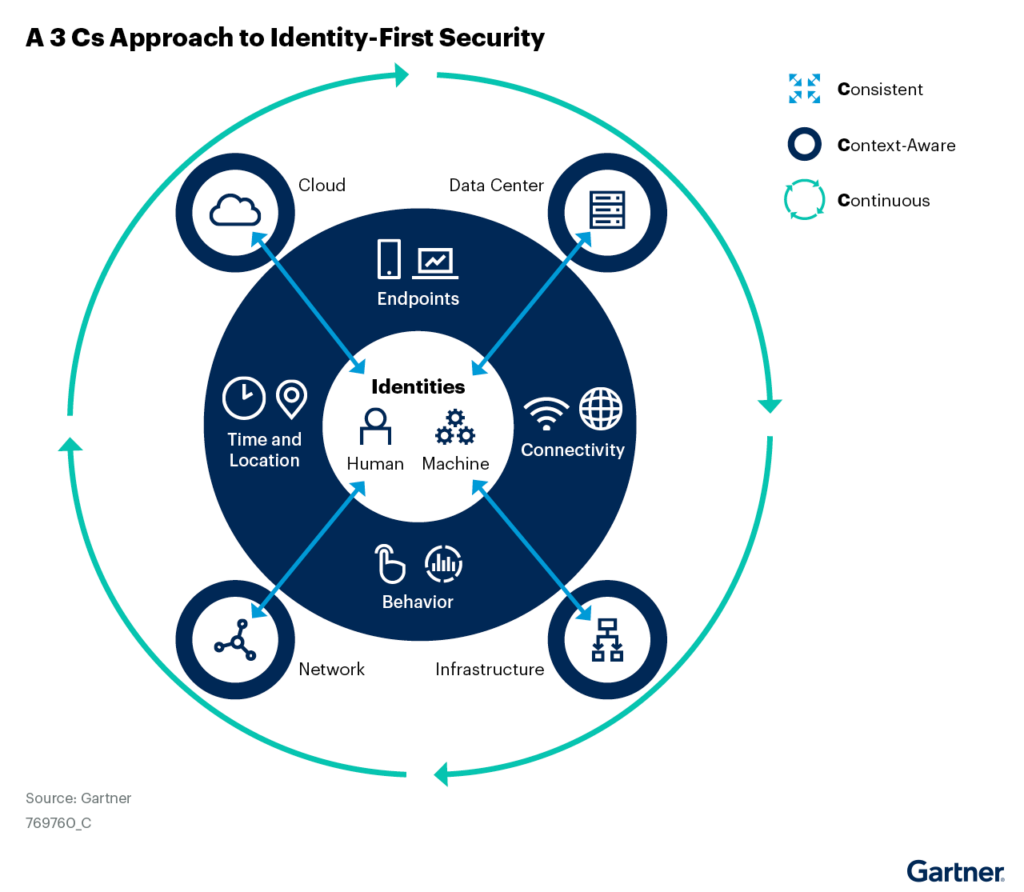
Analysis
Think “Consistent”
IAM is about ensuring that the right users can access the right resources for the right reasons at the right time. In a distributed IT environment, this becomes more important than ever. Traditional enterprise perimeters are based on the understanding that everything inside is “good” and everything outside is “questionable” at best. Once users, assets and data move outside of the perimeter, the whole approach fails, or becomes porous.
Here comes IAM to the rescue. As assets, applications, data and users move outside of the traditional perimeter, access controls must be distributed. These controls rely on IAM to succeed. For example, an API outside of the perimeter needs to be protected by an API gateway. What does this gateway need to do to protect the asset? Enact a policy and utilize information coming from IAM. Another example: Is protecting multiple datasets. Perhaps a data security platform is used to filter, mask and control access to the data. What does this data security platform need to control access? A working IAM system. Thus, in a postperimeter world, IAM becomes the ultimate control and data plane for distributed security.
How does IAM evolve to meet this new responsibility? To achieve an identity-first security strategy, instead of focusing on specific IAM tools, focus on end-to-end flows. This approach moves IAM from a loose hodgepodge of specific solutions to a more open and extensible framework, where tools can be used interoperably. An IAM program is essential to establish control in a consistent, systematic and lasting way.
For example, when applying identity controls for APIs, there are numerous components involved that may include one or more API gateways, an access management (AM) tool, a secrets management tool, public key infrastructure (PKI), and an externalized authorization management (EAM) tool. All of these components need to work together to effectively deliver the control.
Figure 2 illustrates how IAM components can be viewed as elements within a connected ecosystem or identity fabric that enfolds multiple use cases.
Figure 2: Identity-First Security Focuses on Use Cases Instead of IAM Silos
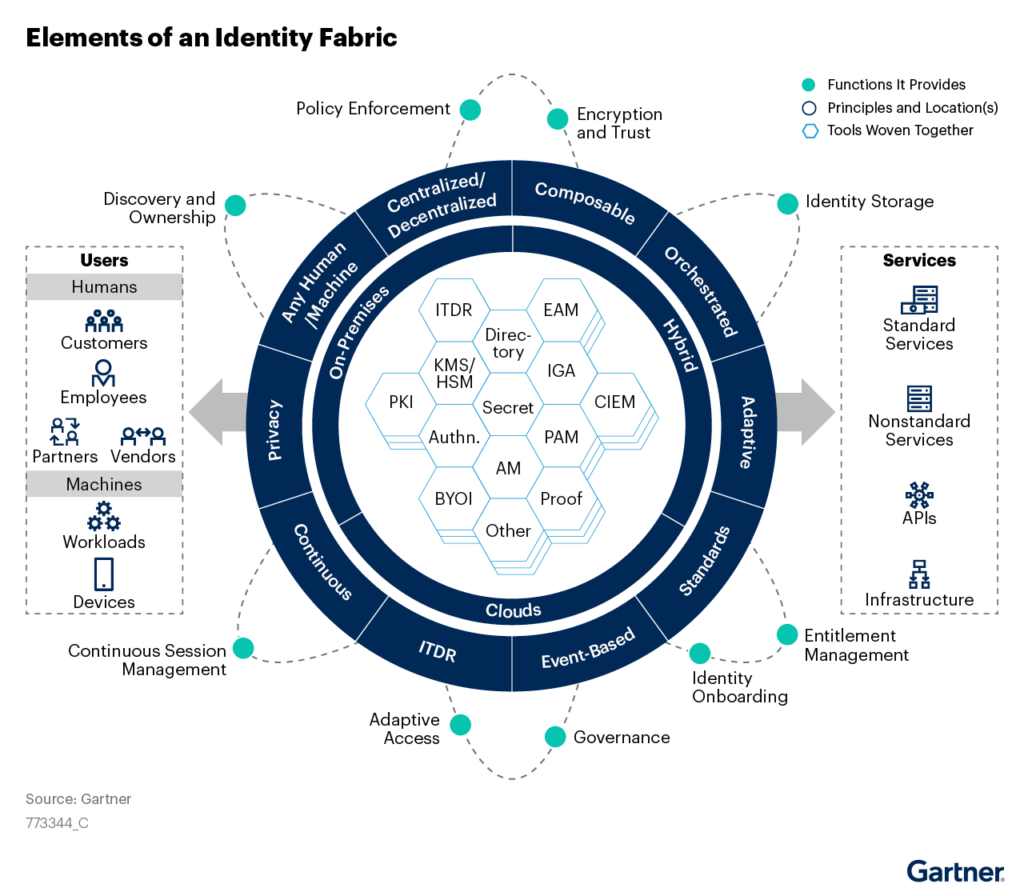
How to Apply Consistent Principles to Identity-First Security
Identity-first security requires centralized policies that need to be extended to decentralized assets. In order to control access to decentralized, distributed digital assets in a consistent manner, IAM leaders must combine centralized IAM controls, policies, data and programs with decentralized and context-sensitive enforcement.
Examples of centralized infrastructure across a distributed environment include:
- Access to multiple SaaS applications
- Managing identity sprawl across multiple clouds — public and private
- Access tokens (“tickets”) managed, renewed and revoked by a centralized AM tool that are locally validated according to policies in decentralized API gateways and protected APIs
Follow these steps, using a consistent mindset:
- Leverage IAM to support zero trust initiatives as a starting point. Zero trust isn’t possible without a solid identity foundation and integrations with identity providers (see Quick Answer: How Do Access Management and Zero Trust Network Access Tools Work Together?).
- Bridge the gaps between the IAM team and business initiatives to ensure that the organization’s security, usability, privacy and scale requirements can be met. Do this by making the identity connection to the organization’s strategic business outcomes by involving stakeholders, as described in IAM Leaders’ Guide to IAM Program Management.
- Include privacy, compliance and data governance representatives in identity-first security discussions, with agreements on how the collection of data will be governed, along with acceptable risk.
- Improve the IAM infrastructure and evolve it to be a more connected, interoperable, agile and smarter identity fabric. Continually improve the identity fabric by viewing use cases individually, taking note of areas within the journey where risk can be introduced or mitigated. Use standards, identity analytics, cross-functional team structures and best practices for how to integrate and use the functions of the identity fabric (see How to Start Building a Cybersecurity Mesh Architecture).
- Leverage advanced analytics, such as policy violation analysis and anomaly detection, to identify user access that differs from the peer group. Identity analytics plays an important role in identity-first security. Eliminate unused access by correlating usage analytics to see if the currently assigned access rights, including access granted using nested roles, have been used by the identity within the organization’s defined thresholds.
- Integrate user risk scoring based on identity events with other security intelligence or analytics frameworks within the organization (for example, pulling data from user entity and behavior analytics [UEBA] within a security information and event management [SIEM] tool and combining it with risk analytics from a zero trust network access [ZTNA] tool).
Think “Context”
Context refers to the attributes describing a user (someone or something) and an asset, and how that user is trying to access the asset. It also includes interesting events, state information and variables that can signal trust or potential risk. Context applies to both human and machine identities, and it is time to think differently about how additional attributes can be added to existing IAM policies. For example:
- An account has not been used for seven months, but it is still active.
- The device used is different from one used previously, the software release is not current or there are known vulnerabilities.
- The date, time, location or network link is inconsistent with, or does not fit the usual patterns for, that user.
- A user’s safety training certification has expired, but that user still has access to a critical application.
- The user context is out of the ordinary. Language preferences and time zones may have changed, with no associated change in location.
- A user’s behavioral context and access patterns, if known, are considered (e.g., Is this a perfectly normal or an atypical request?).
- A user’s reputational context, if known, is considered (e.g., Does this come from a known good, or bad, IP address?).
From an employee use-case perspective, it is common to evaluate a simple set of attributes, such as endpoint device identity, network identity, time and date (whether the employee is working during business hours), and geolocation. As the user journey progresses, additional signals can be gathered, such as behavioral data (e.g., how the user navigates within an app) or passive behavioral biometrics (e.g., typing, gesture handling), with advanced analytics including machine learning (ML), which enables adaptive access decisions using AM tools and centralized policies.
How to Apply Contextual Principles to for Identity-First Security
To begin this journey, it is important to understand what context data is available, where it is collected and mastered, and how trustworthy it is. The collection of context data can come from a variety of sources, depending upon the specific use case.
IAM is ideal to manage and curate the context, and distribute it to the actual access controls. For example, signals can be applied to help with mitigating the risks from unused accounts, entitlements, and uncertified access. Anomalies based on peer group analysis, privilege elevation outside privileged access management (PAM), privileged activities performed by identities with no approvals or access added outside provisioning workflows can also create triggers for remedial action. Other events that provide valuable context could include expired attestations, self-approved access or self-certified access, or if an identity is inactive but has accounts in target systems that are in use.
Some other common sources of data for managing and tracking context include:
- Cloud infrastructure entitlement management (CIEM) tools, which create a centralized visualization of access paths to protected cloud assets, and a monitored baseline of acceptable usage of access rights, to reduce the attack surface.
- SIEM systems, designed to aggregate, normalize and collate security-related data from a range of devices, including (but not limited to) endpoints, network devices, servers, applications and cloud infrastructure. These are a wide range of management services that allow for monitoring and alerting of potential security issues.
- ZTNA tools, which typically depend on signals from IAM tools for user/account context and other tools for device context.
- Online fraud detection (OFD) tools, which can provide insight that detects and prevents wrongful or criminal deception within web and mobile digital B2C channels.
- Endpoint, network and extended detection and response (EDR, NDR and XDR) tools, which can provide alerts by integrating with identity events.
Follow these steps, using a contextual mindset:
- Look for ways that external events can trigger actions based on context. Some examples may be identity governance and administration (IGA) tools and processes, terminating a single sign-on (SSO) session or blocking access to a vault in PAM. These could be automated actions, such as a micro certification event or an emergency lockout.
- Evaluate your organization’s authorization strategy (likely, it is very fragmented) and look for opportunities to provide centralized policy administration and decentralized enforcement. EAM tools can help bridge those gaps. Be sure to include dynamic context in authorization decisions.
- Integrate user risk scoring based on identity events within other security intelligence or analytics frameworks within the organization.
Think “Continuous”
The threat landscape continues to be more difficult to navigate, and trust decisions become more essential. Traditional one-time gating mechanisms (once you’re in, you’re in) are insufficient to cater to this new reality. Trust and risk must be assessed at every moment, and changes must be reflected immediately, across all sessions. For this reason, IAM is well-placed to deliver a more continuous approach to support an adaptive zero trust security capability.
Manual Process Steps Versus Continuous, Automated Governance
Many IAM activities are workflow-driven. For example, a request for access is evaluated by a supervisor who either grants or rejects the request. A similar event happens with access certification campaigns; many organizations run these as massive exercises during certain times of the year. Discovery processes are run at certain intervals to find new accounts or assets, or to identify discrepancies from the expected state of accounts and access rights. Yet, by the time that certification campaigns, discovery processes or access recertifications conclude, they may already be out of date. How quickly can an organization react should something change?
The answer to that question is usually unsatisfactory. Access decisions need to be made quickly and wisely, and potentially changed rapidly to react to an active threat. Identity governance is required, yet most IAM deployments are still so process-driven that they cannot react quickly. A change in thinking is critical here, and the key is to move toward a continuous governance style that is able to adapt quickly to change.
Static Versus Dynamic
Historically, authorization decisions are based on static access rights, and typically include access control lists or predefined roles that are assigned by an administrator (i.e., decisions are essentially fixed at admin-time). A more adaptive approach, or one that is more dynamic in nature, builds on the concept of risk-based authentication along with context-aware authorization to provide a flexible approach to access control (i.e., varying decisions can be made at runtime). These controls enforce policies that are inherently contextual and dependent on entities’ relationships and states. These policies cover a wide range of security, compliance or business rules governing the operation of an organization.
Continuous controls can be applied at both admin-time and runtime. With admin-time, policies are continuously reviewed and updated occasionally when required, while runtime uses ongoing analytics to modify access decisions.
Multifactor Authentication Versus Journey-Time Orchestration
As defined in Innovation Insight: Journey-Time Orchestration Mitigates Fraud Risk and Delivers Better UX, it is important to assess risk across the entire user journey to understand which signals are of interest per event, along with defining policies as the journey progresses. This is different from applying multifactor authentication at only the beginning of the journey.
User experience (UX) is a key consideration, and improvements can be made by progressively evaluating recognition and risk signals throughout the session. Adaptive access control means that traditional access control restrictions (such as the need to always use an intrusive higher-trust user authentication method) can be relaxed while risk is low, thus improving UX.
How to Apply Continuous Principles to Identity-First Security
Some examples where continuous principles can be applied include:
- Continuous adaptive trust (CAT) can be applied for workforce, customers and partners, superseding legacy multifactor authentication flows. CAT consumes credentials and recognition and risk signals (behavioral data, contextual data and passive behavioral biometrics) to establish trust in an identity claim, and acts to adjust the trust level dynamically.
- Continuous role management, ensuring near-real-time role definition accuracy by removing unused entitlements from a role.
- Continuous access reviews, which could be triggered when an employee’s access behavior changes or when a user’s risk level crosses a particular threshold. A microcertification event could allow a reviewer to focus on the most relevant information to certify, rather than using a bulk approach for certification.
- Continuous scanning for rogue or orphan accounts to minimize detection time to almost real time.
- Continuous session management, using Continuous Access Evaluation Profile (CAEP; see the profile in Hype Cycle for Digital Identity, 2022), which enables IAM infrastructure tools, and the services they protect, to continually share security events within a session to continuously reinforce policies in a decentralized environment in a dynamic way.
- Continuous detection of unauthorized changes as an effective way of improving controls for identity threats (identity threat detection and response [ITDR]).
Follow these steps, using a continuous mindset:
- Deploy tools and methods for continuous discovery of assets, accounts and permissions, rather than running them only during audit cycles.
- Enable event-based micro certification, where a change in state will trigger a very targeted review of only the affected users and their access rights.
- Use journey-time orchestration (JTO) technology to tie multiple tools and technologies into a cohesive security solution that integrates with the user’s journey as seamlessly as possible.
- Enable just-in time (JIT) privileged access where possible (see Reduce Risk Through a Just-in-Time Approach to Privileged Access Management).
Common Pitfalls When Implementing Identity-First Security
These common pitfalls include:
- Legacy IAM architecture continues to lack flexibility and full interoperability (which are necessary properties of an identity fabric).
- IAM maturity continues to average an IT Score of 2.4 out of 5,1 which implies that most organizations continue to struggle to meet basic identity controls and still have automation challenges.
- Risk tolerance acceptance decisions need to be agreed on at an enterprise level. Often, policy decisions are made within security and IT, without involving the wider organization (see Predicts 2022: Identity-First Security Demands Decentralized Enforcement and Centralized Control).
- As discussed in Hype Cycle for Digital Identity, 2022, CAEP is a new standard, and is still not commonly known and understood by IAM experts.
Evidence
Identity-first security was introduced by Gartner in early 2021 in Top Security and Risk Management Trends 2021, and is often discussed in client inquiries and vendor briefings.
Industrywide references to identity-first security include:
5 Minutes With David Mahdi — Establishing Digital Trust With Identity-First Security, Security magazine.
Sensible 2022 Resolutions for Behavioral-Aware, Identity-First Security, Identity Defined Security Alliance (IDSA).
The Path to Zero Trust Starts With Identity, IDSA.
1 Based on Infographic: Benchmark Data From the IT Score for Identity and Access Management.
Acronym Key and Glossary Terms
| CAEP | Continuous Access Evaluation Profile |
| CAT | continuous adaptive trust |
| CIEM | cloud infrastructure entitlement management |
| EAM | externalized authorization management |
| EDR | endpoint detection response |
| IGA | identity governance and administration |
| ITDR | identity threat detection and response |
| JTO | journey-time orchestration |
| NDR | network detection response |
| OFD | online fraud detection |
| PAM | privileged access management |
| SIEM | security information and event management |
| SSO | single sign-on |
| UEBA | User entity and behavior analytics |
| UX | user experience |
| XDR | Extended detection and response |
| ZTNA | Zero trust network access |
Note 1: What Do We Mean By Decentralized?
The key feature of a distributed identity fabric is that it supports all digital assets owned by an organization, regardless of their location.
© 2023 Gartner, Inc. and/or its affiliates. All rights reserved. Gartner is a registered trademark of Gartner, Inc. and its affiliates. This publication may not be reproduced or distributed in any form without Gartner’s prior written permission. It consists of the opinions of Gartner’s research organization, which should not be construed as statements of fact. While the information contained in this publication has been obtained from sources believed to be reliable, Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information. Although Gartner research may address legal and financial issues, Gartner does not provide legal or investment advice and its research should not be construed or used as such. Your access and use of this publication are governed by Gartner’s Usage Policy. Gartner prides itself on its reputation for independence and objectivity. Its research is produced independently by its research organization without input or influence from any third party. For further information, see “Guiding Principles on Independence and Objectivity.” Gartner research may not be used as input into or for the training or development of generative artificial intelligence, machine learning, algorithms, software, or related technologies.
















