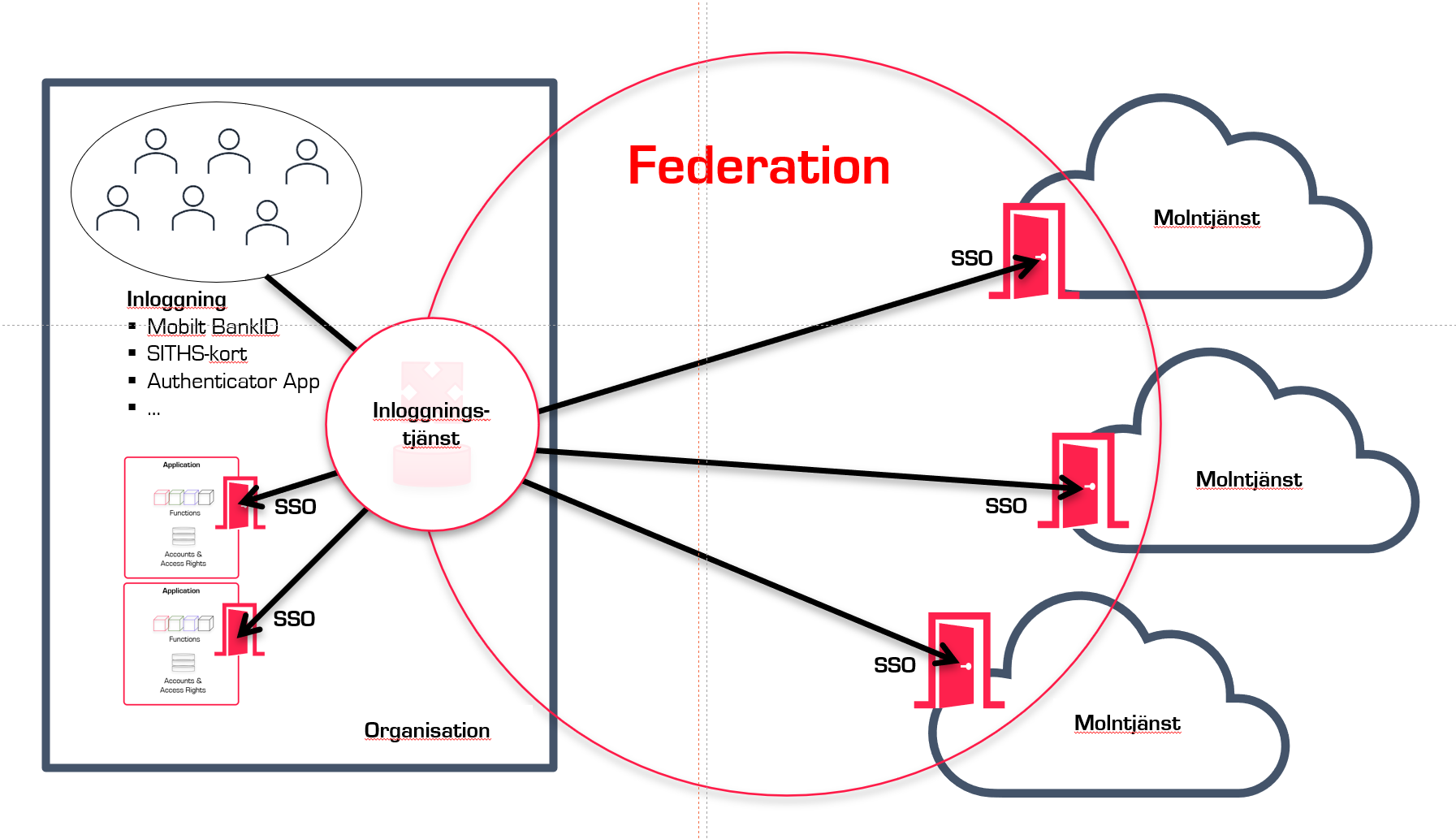
Do you have sufficient protection?
Information is typically made available through systems or services, and providers often have good and purposeful features for presenting and processing information. However, the need for protection varies with different types of information. Sometimes, systems and services have built-in protection that is sufficient, while other times it may be inadequate.