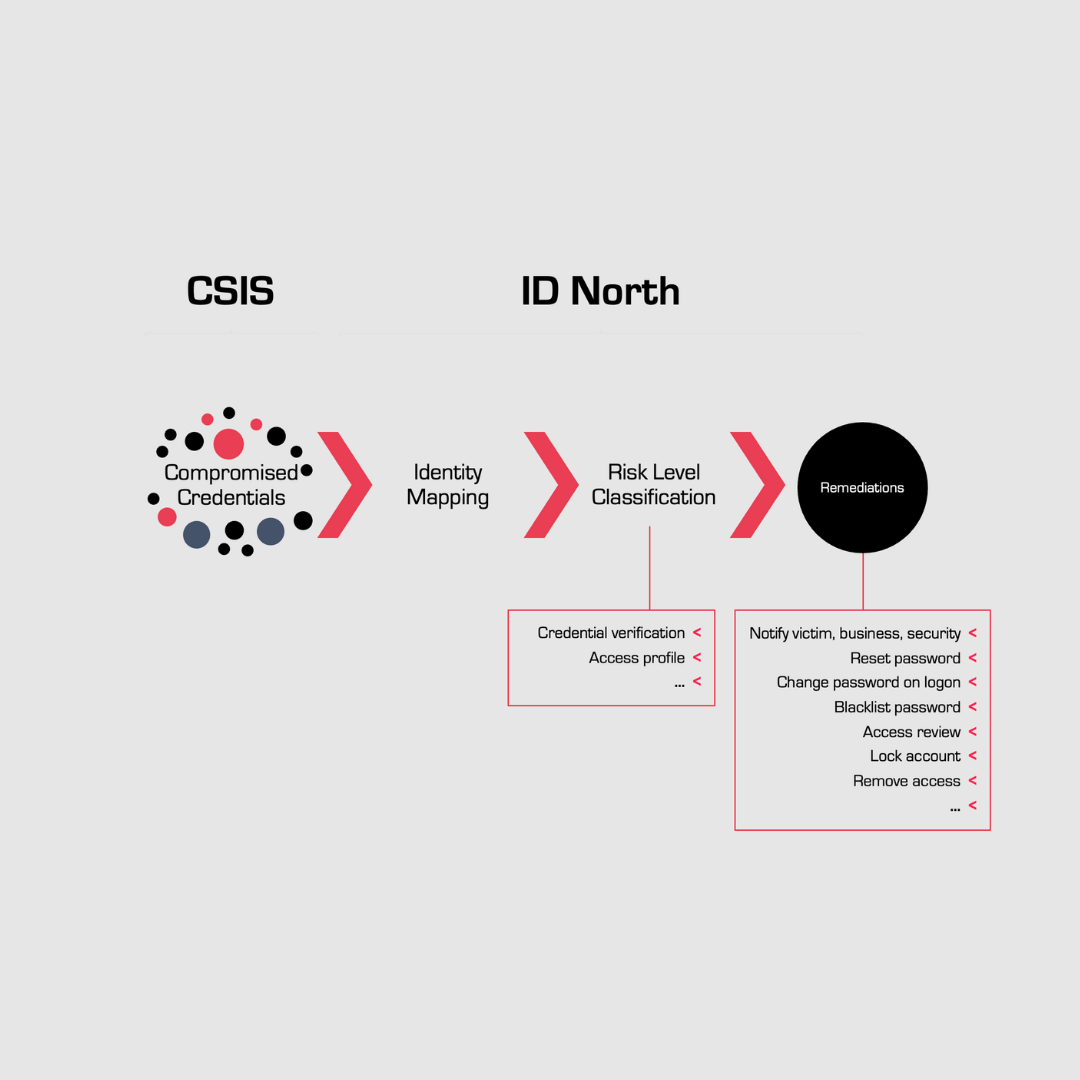
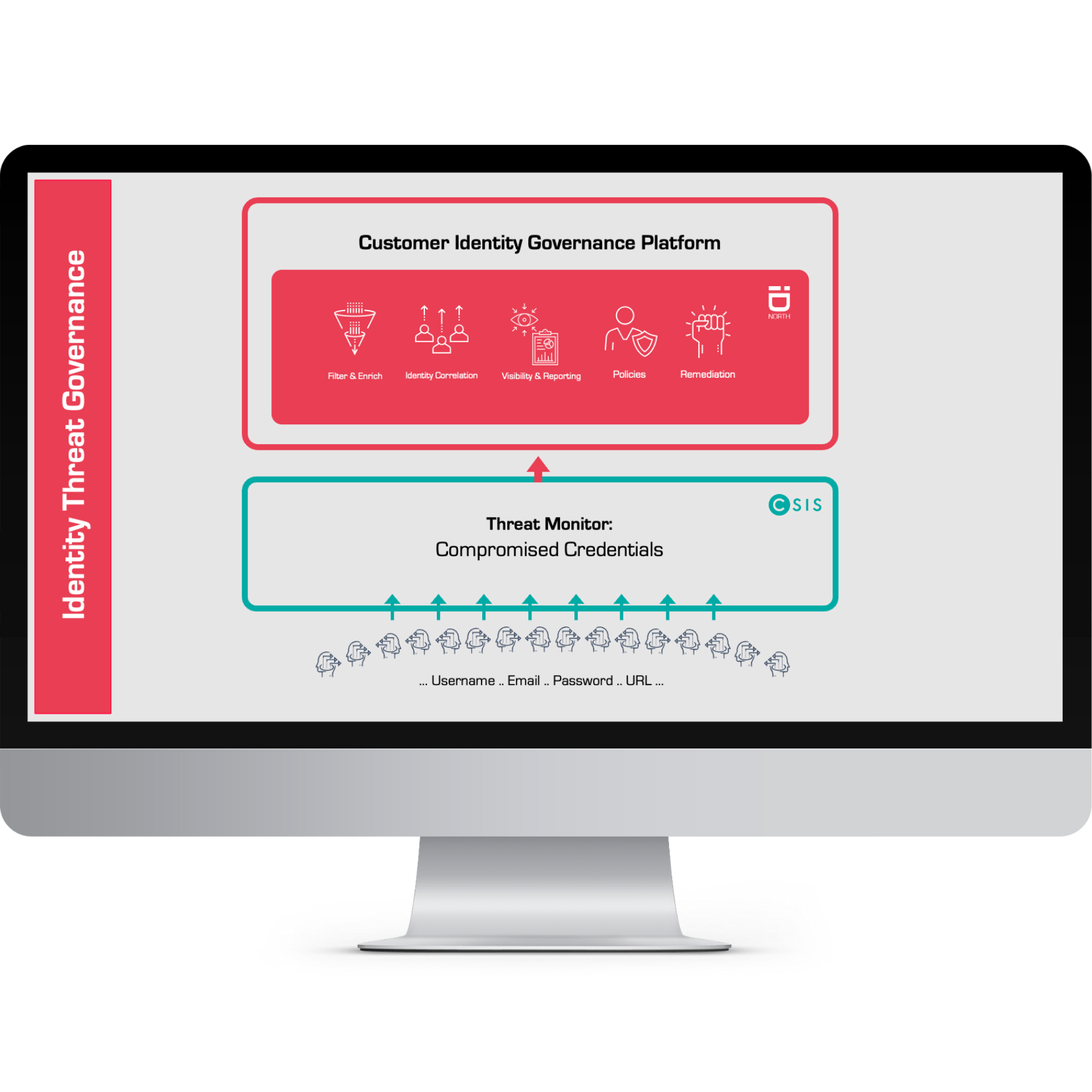
Identity Threat Governance™
Did you know that credentials from your organization could be for sale on the dark web right now?
With Identity Threat Governance™, we go beyond traditional identity security. Our service actively scans the dark web to uncover stolen credentials and takes immediate action—closing compromised accounts, securing access, and preventing further damage.
By combining Identity Governance with Threat Intelligence, we help your business stay ahead of cybercriminals, safeguarding your systems, data, and reputation.
A strong identity security strategy protects your organization by governing access and ensuring the principle of least privilege applies to employees, partners, and customers alike. While Identity Threat Governance continuously identifies external threats, Identity Governance restricts access, assigns risk scores, and aligns permissions with roles and tasks. Together, these services create a robust defense to keep your organization secure.